Trezor Bridge – The Complete Guide to Secure Hardware Wallet Connectivity
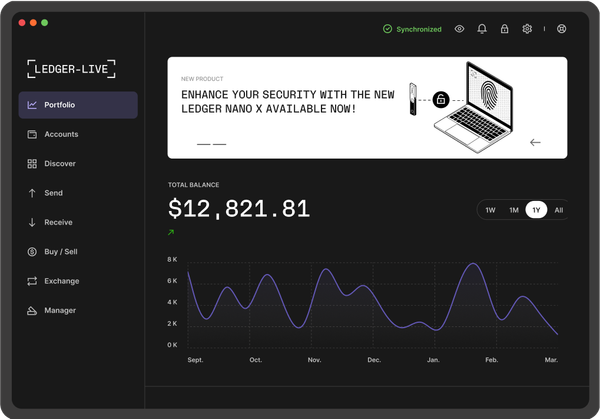
In the world of cryptocurrency security, hardware wallets are considered the gold standard for protecting digital assets. However, even the most secure hardware device needs a reliable way to communicate with your computer and browser. That’s where Trezor Bridge plays a critical role. Designed to enable seamless communication between your Trezor hardware wallet and your web browser, Trezor Bridge ensures secure, smooth, and efficient crypto management.
If you use a Trezor device, understanding Trezor Bridge is essential for maximizing security and performance.
What Is Trezor Bridge?
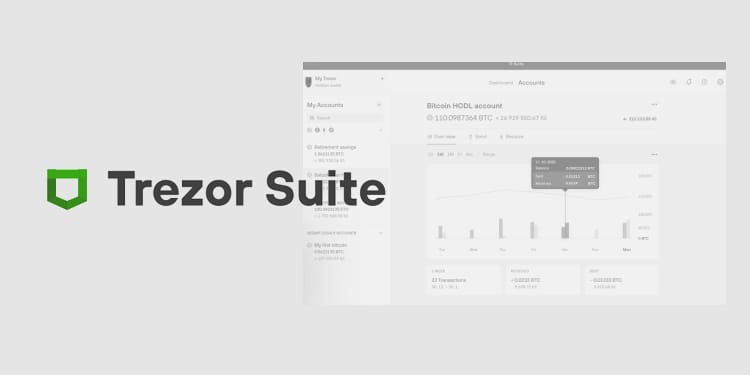
Trezor Bridge is a background software application that allows your web browser to communicate directly with your Trezor hardware wallet. It acts as a secure connector between your device and the official wallet interface at Trezor Suite or supported third-party platforms.
In simple terms, Trezor Bridge ensures that your hardware wallet and browser can “talk” to each other safely without exposing your private keys or sensitive information.
Unlike browser extensions, Trezor Bridge runs quietly in the background after installation. It automatically detects when a Trezor device is connected and facilitates secure communication.
Why Trezor Bridge Is Important
Security in crypto is everything. Trezor Bridge enhances the safety and reliability of your hardware wallet experience in several key ways:
1. Secure Communication Layer
Trezor Bridge creates a secure channel between your hardware wallet and browser-based interfaces. It ensures that transaction data is transmitted safely while private keys never leave the device.
2. Improved Browser Compatibility
Earlier, users relied on browser extensions to connect hardware wallets. Trezor Bridge replaces that approach with a more stable and secure background service, reducing compatibility issues across browsers like Chrome, Firefox, and Edge.
3. Seamless User Experience
Once installed, Trezor Bridge works automatically. There’s no need to manually launch it each time you connect your device. This makes crypto transactions smoother and more convenient.
How Trezor Bridge Works
When you plug in your Trezor hardware wallet — such as the Trezor Model One or Trezor Model T — Trezor Bridge detects the device through your computer’s USB connection.
Here’s what happens behind the scenes:
- The browser requests communication with the Trezor device.
- Trezor Bridge securely verifies and establishes the connection.
- Transaction details are sent to the device for confirmation.
- You physically confirm the transaction on your hardware wallet.
- The signed transaction is returned safely to the browser.
At no point do your private keys leave the hardware wallet. This is what makes hardware wallets — combined with Trezor Bridge — significantly more secure than software-only wallets.
Key Features of Trezor Bridge
Automatic Device Detection
The software automatically recognizes when your Trezor is connected.
Background Operation
Runs silently without interrupting your workflow.
Cross-Platform Support
Compatible with Windows, macOS, and Linux operating systems.
Enhanced Stability
Provides more reliable connectivity compared to older browser extension methods.
Continuous Updates
Maintained by SatoshiLabs, the creator of Trezor, ensuring ongoing security improvements.
Installing Trezor Bridge
Installing Trezor Bridge is simple:
- Visit the official Trezor website.
- Download the version compatible with your operating system.
- Install the application.
- Restart your browser.
- Connect your Trezor device.
After installation, Trezor Bridge runs automatically whenever needed. There’s no complicated setup process, making it beginner-friendly.
Is Trezor Bridge Safe?
Yes, Trezor Bridge is considered highly secure when downloaded from the official source. Since it is developed and maintained by SatoshiLabs, it follows strict security protocols.
However, always ensure:
- You download it only from the official Trezor website.
- Your operating system is up to date.
- You verify website authenticity to avoid phishing attempts.
Remember, Trezor Bridge does not store private keys or crypto funds. It simply facilitates communication between your device and wallet interface.
Trezor Bridge vs Browser Extensions
Previously, hardware wallets relied on browser extensions for connectivity. However, browser extensions can sometimes pose compatibility risks and security vulnerabilities.
Trezor Bridge offers:
- Better performance
- Reduced browser conflicts
- Improved security architecture
- Long-term support and updates
This shift to a standalone background application represents a major upgrade in hardware wallet connectivity.
Who Should Use Trezor Bridge?
If you own any Trezor hardware wallet, Trezor Bridge is essential. It’s especially important for:
- Long-term crypto investors
- Security-focused users
- DeFi participants using hardware wallet protection
- Anyone managing large crypto holdings
Without Trezor Bridge, your browser may not properly recognize your Trezor device.
Final Thoughts
Trezor Bridge may run quietly in the background, but its role in crypto security is powerful. By enabling encrypted communication between your browser and hardware wallet, it strengthens your overall protection strategy.
When combined with a Trezor device and Trezor Suite, Trezor Bridge forms a highly secure ecosystem designed to protect your digital wealth.